
PerfectData Software was originally developed as a legitimate tool for email migration, data recovery, and mailbox backups. It assists businesses in securely transferring and preserving critical information. However, cybercriminals have recently used a PerfectData Software Exploit to infiltrate Microsoft 365 accounts. Using it to leverage its access permissions to gain unauthorized control over user data. In this specific case it was used to trigger a Dropbox Phishing Attack
By registering PerfectData Software within a target’s Azure Active Directory (Azure AD), attackers can grant it permissions to read and extract email data—effectively bypassing traditional security measures. This technique allows them to exfiltrate sensitive information, monitor user communications, and launch further attacks, often without raising immediate red flags. Given Microsoft 365’s widespread use in businesses of all sizes, this exploitation presents a serious cybersecurity risk.
In this article, we’ll break down how the PerfectData Software Exploit is being used, the specific security vulnerabilities it exploits, and most importantly, how you can protect your Microsoft 365 environment. Whether you’re an IT administrator or a business owner, staying informed about these evolving threats is essential for safeguarding your data and preventing unauthorized access.
PerfectData Software Exploit as a New Attack Vector for Dropbox phishing attack
Last week, we observed an attack using the PerfectData Software Exploit to first gain access to the victim’s Microsoft Office 365 email account, then leverage that access to compromise Dropbox. The breach first came to our attention when multiple recipients received an unexpected Dropbox file share invitation from a compromised account. This was an unusual behavior for that particular user, raising immediate suspicion.
While investigating, another user at the same site reported receiving the same message. Upon closer inspection, the shared file was a legitimate PDF document containing a deceptive link labeled “Get Document.” Clicking the link redirected users to a document stored in Google Docs, which in turn prompted them to “View File in OneDrive.”
PerfectData Software Exploit-Dropbox Phishing Attack Plan
Step 1: Fake Microsoft 365 Sign-In Page
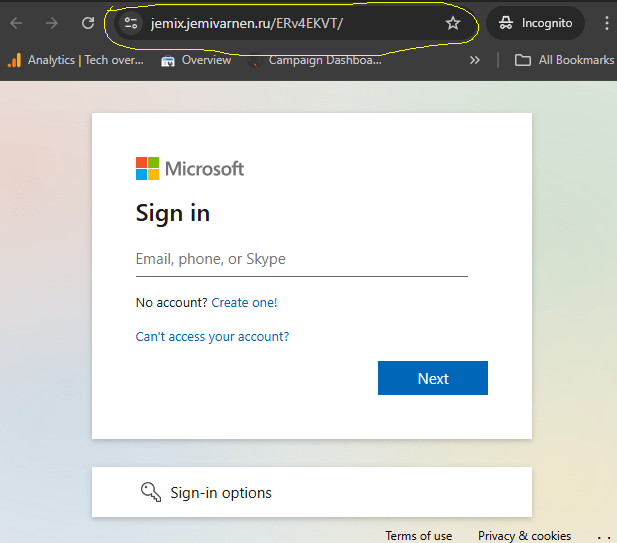
The final destination of the phishing link was a spoofed Microsoft 365 sign-in page. A closer inspection of the browser’s address bar revealed that it was actually hosted on a Russian domain, indicating a fraudulent attempt to harvest credentials.
Step 2: Exploiting PerfectData Software in Microsoft 365
Checking the Microsoft 365 Sign-In Activity, we found unauthorized login attempts originating from Miami, which the affected user did not recognize. Despite having multi-factor authentication (MFA) enabled, the attacker successfully bypassed it, likely using a third-party application injected into Office 365.
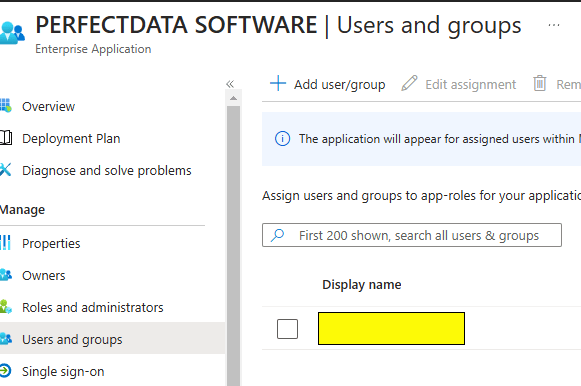
Upon further investigation in Microsoft Entra Admin Center, we identified a suspicious Enterprise Application labeled “PerfectData Software.” This application had been granted elevated permissions to the compromised account. We confirmed that it had been installed three months earlier, and the attacker had been dormant for that period.
Step 3: Manipulating Email Rules and MFA
After compromising the Microsoft 365 account, the attacker used the PerfectData Software Exploit:
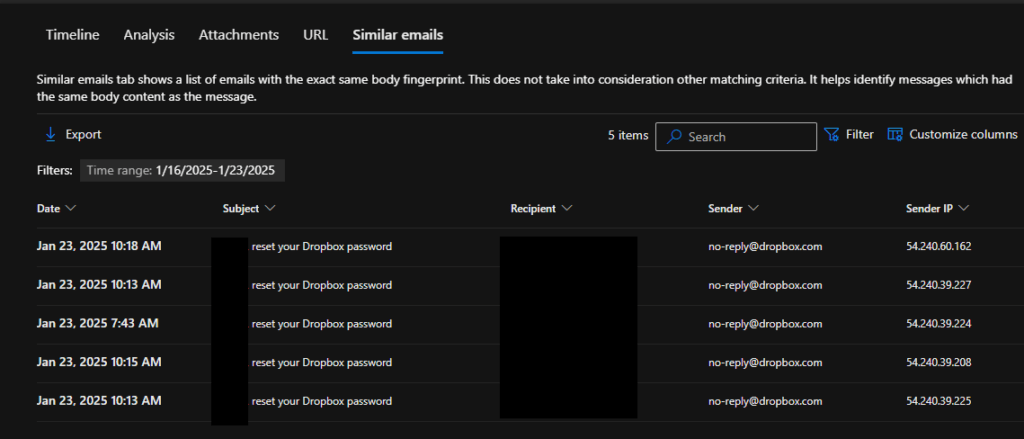
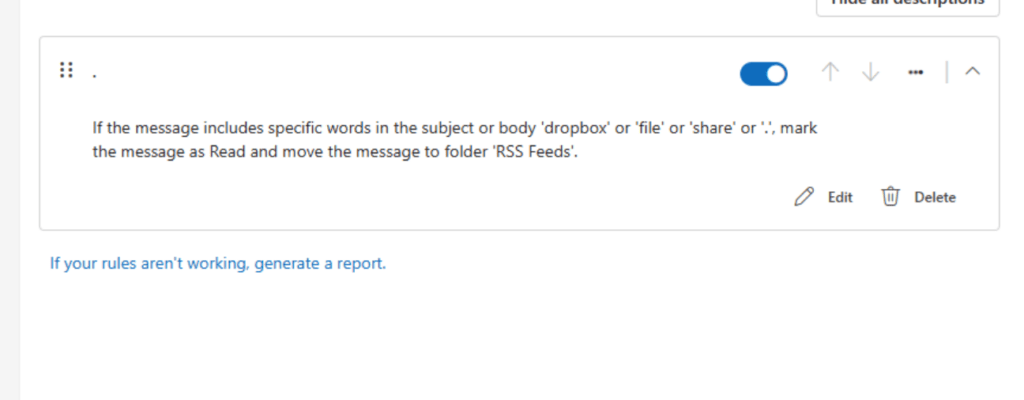
- Created a malicious Exchange mail rule redirecting all mail to the RSS Feeds folder.
- Requested a password reset for the victim’s Dropbox account.
- Logged into Dropbox and changed the password and added MFA to the account.
- Uploaded the malicious PDF document.
- Exfiltrated a target list from the mail account of the victim
- Shared the malicious file with targeted email list.
Securing the Compromised Accounts From the PerfectData Software Exploit
After identifying the attack vector, we took the following steps:
- Removed the unauthorized PerfectData Software Exploit from Microsoft 365.
- Deleted the malicious Exchange rule redirecting emails to the RSS Feeds folder.
- Restored the user’s inbox and manually processed the Dropbox password reset email.
- Attempted to log into Dropbox, only to find that the attacker had already enabled MFA on the compromised account.
- Submitted a request to Dropbox Support to temporarily suspend the account and regain control.
- Confirmed a similar breach attempt occurred three months prior, showing the attack had been lying dormant.
Contact Us if you need assistance with this!
Conclusion
The PerfectData Software Exploit used in the Dropbox Phishing Attack highlights the increasing sophistication of modern cyber threats. Attackers exploited third-party application permissions, mail rules, and MFA weaknesses to maintain long-term access to compromised accounts. By understanding how this attack unfolded and implementing proactive security measures, businesses can significantly reduce the risk of similar incidents.
Organizations must continuously monitor their security posture, audit third-party applications, and educate users about social engineering tactics. The threat landscape is constantly evolving, and only by staying vigilant can businesses effectively protect their critical data and cloud environments.
Our Notes from the Dropbox Phishing Attack Discovery…..
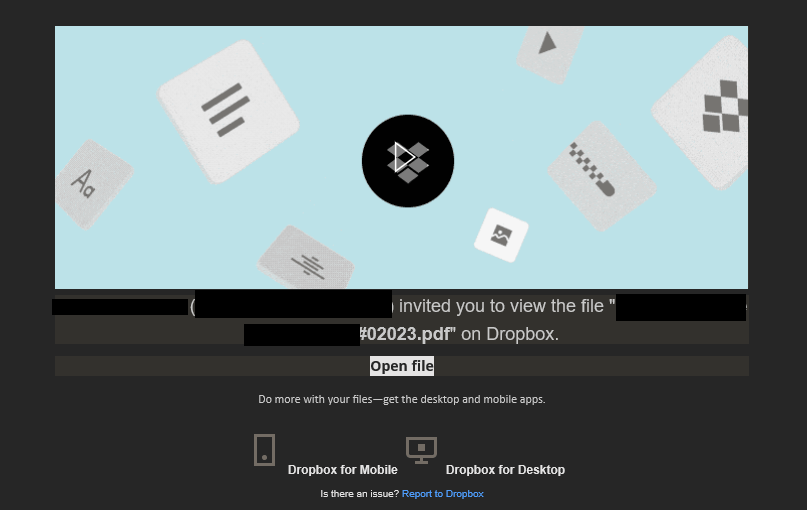
We accessed the shared file from a ‘sandboxed’ machine and found that it was a legitimate PDF file with a ‘Get Document’ link. After clicking the link we were redirected to a document stored in Google Docs That only had an option to ‘View File in OneDrive’


The link led to what appeared to be the Microsoft Office 365 SIgn On Landing Page. However, upon closer inspection the address bar was pointed to a Russian domain. With the exception of the domain the mirrored landing page was near perfect.
Altered Exchange Rules
We then attempted to log into the Dropbox account in order to remove the file share and found that the credentials did not work. Then sent a password change request and never received the password reset email from Dropbox. I logged in as an Exchange administrator and checked the mail flow and found that the message was reported as delivered, however, we also noticed that there was a password reset request that we did not send earlier in the morning.
We next logged into Outlook Web Access to determine why the mail was not delivered and identified the following Exchange Rule that was redirecting all of received messages to the ‘RSS Feeds’ folder.
We deleted the rule and moved the messages to the Inbox. At this point we were able to access the reset email and reset the password to Dropbox. However, we found that MFA had been added to the account and were unable to authenticate.
Unauthorized Access to O365
Checked the Microsoft 365 sign in activity for the user. We found several sign on events that were not recognized from Miami.
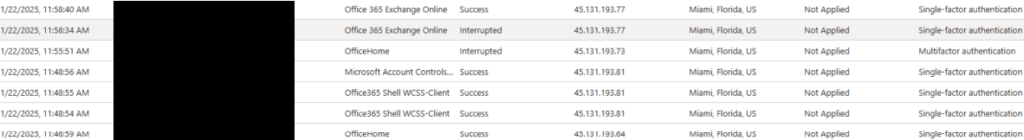
The user did have MFA enabled for their account. So the question was ‘How did the attacker bypass MFA?’ After finding the faux landing page, I began to suspect that a 3rd party application had been injected into Office 365. We logged into the Microsoft Entra Admin Center for the MS 365 Tenant. Then we checked under Applications->Enterprise Applications and found an application that was not recognized…. “PerfectData Software”. It did not take extensive research to determine that this was the culprit. The application was installed in late October (three months ago.) The only user with access to the PerfectData Application was the affected user. We removed the application after memorializing the information.
Securing Accounts
At this point we had secured the Microsoft 365 account, and the Dropbox account. However, we still were unable to access the Dropbox account due to MFA. A ticket was reported with Dropbox. We requested that the account be placed in suspense until the ticket was closed. It required 7 days to restore access to the account. At the time access was restored we reviewed the history on the account and found that there was an identical file shared with the user on 10/29/24. The attacker had successfully breached the account 3 months prior and remained dormant for that time.

